Obtain Valuable Data from Images Using Exif Extractors.
Hello guys,
I hope you all are good at your home.
Today's topic is How To Obtain Valuable Data from Images Using Exif Extractors. So Let's go. What is Metadata?
- Metadata contained in images and other files can give away a lot more information than the average user might think.
- By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.
- For hackers or OSINT researchers gathering digital evidence, photos can be a rich source of data. Besides what's visible in the picture itself, metadata about when and where the photo was taken can also be recoverable.
- This data can include the device the photo was taken on, the geolocation of the image, and other unique characteristics that can fingerprint an image as haven been taken by the same person or device.
- Metadata, or the data that describes files like images or videos, is useful during reconnaissance to investigators because it's often overlooked by otherwise careful targets.
- If people don't know what kind of data can be retained in a particular file format, they won't know if they're putting themselves at risk by making a specific file public. While many social media platforms have largely eliminated this problem by stripping out metadata from files, there are still many images online with this data left entirely intact.
- Metadata, or the data that describes files like images or videos, is useful during reconnaissance to investigators because it's often overlooked by otherwise careful targets.
- If people don't know what kind of data can be retained in a particular file format, they won't know if they're putting themselves at risk by making a specific file public.
- While many social media platforms have largely eliminated this problem by stripping out metadata from files, there are still many images online with this data left entirely intact.
- Exchangeable image file format data, or Exif data, is information that accompanies image files and offers many fields that can be populated or left blank.
- The information is used by programs to understand better what is contained inside the file to aid in sorting and other functions.
- Available data fields in Exif are often written to by the device that took the image at the time it was shot but can also be left by processing programs like Photoshop.
- Because we can often identify the model of camera used, the settings used, and supplementary information like the owner of the software that made Photoshop changes, it's possible to identify images that came from the same source.
- The more Exif fields are filled out by the device that shot the image or software that processed it, the easier it is to track other files made by the same process.
So, now let's begin the journey..
Method-1: Use Jeffrey's Image Metadata Viewer Web App
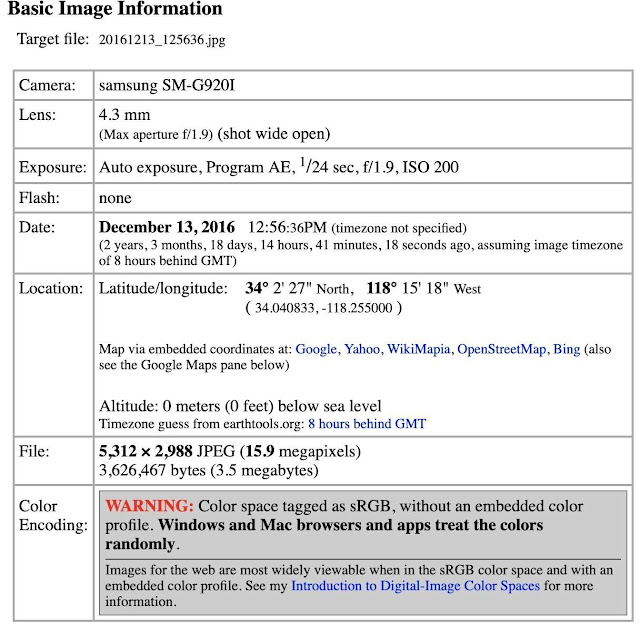
- If you're using a browser, there are two great free websites to extract Exif data. First, let's start with Jeffrey Friedl's Image Metadata Viewer.
- The site does not use HTTPS, unfortunately. If you don't mind that, you can see the simple design is easy to use and supports a vast variety of formats, unlike the command line tool which only works with JPG files.
- So you can scan RAW image files like CR2 and DNG, PNG, and TIFF, to name a few. Upload a file or add its public URL, check the CAPTCHA, and hit "View Image Data."
Method-2: UseVer Exif's Web App
- Our second website, Ver Exif at verexif.com, spits out all of the Exif data after a scan, but it also comes with an option to strip metadata out of images.
- Removing the metadata is useful if you want to make sure an image you're sending doesn't contain data you didn't intend to send.
- To view Exif information, upload a file or add its public URL, then hit "View Exif." In my example, passing the same photo into this website, the output is much less, but it generates a handy map of where the photo was taken.
- The information is accurate, but not as big of a data dump as the Image Metadata Viewer web app.
- Interestingly, after I passed the test photo through the "Remove Exif" data option, I uploaded it to the first website to see if the metadata was truly removed.
- It turns out I can still tell it was taken on a Samsung device, so I don't recommend using this tool to strip metadata from your photos.
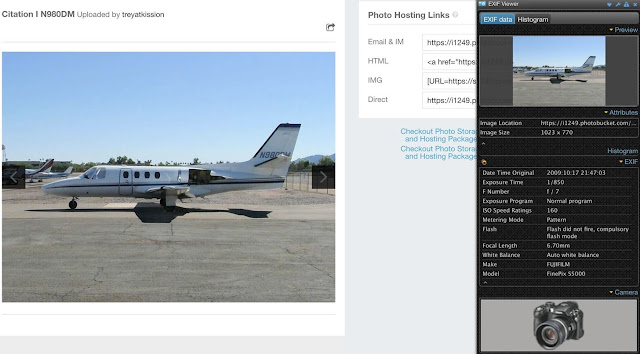
Method-3: Use EXIF Viewer Chrome ExtensionApp
- In Google Chrome, you can install the EXIF Viewer extension, which will let you pull up the Exif data from any photo you load into the browser.
- Using browser add-ons to extract Exif data is even simpler than using a web-based tool.
- After installing and enabling the plug-in, we can right-click any image in the browser and select "Show EXIF data" to reveal any information the image contains.
- To test this out, I found a random image on a photo-sharing website and looked through the metadata provided by EXIF Viewer to find the type of camera that was used to take it.
Metadata Reveals the Story Behind a Photo
- While a photo may yield valuable information, the real value may be in what's encoded in the metadata. Accessing this data is easier than ever, so it's essential to be aware of what information you may be giving away when you send a photo.
- While many social media platforms and photo-hosting services do you the favor of stripping out this data, not all do.
- It's important to make sure you're not leaking this data if you don't intend to, and these tools can quickly help you identify any ways you might be leaking your location or other private data in photos you want to share online.
- Most importantly, make sure to disable geo-encoding on your phone if you don't want GPS coordinates burned into every image you take.
NOTE:- Guys, if you can't understand anything just write
it below in the comment section, I will try my best to explain you or you can contact me at hackingtips90@gmail.com





Comments
Post a Comment